Edge computing vs fog computing is becoming a frequent discussion as cloud computing gains popularity and people rely on more Internet of Things (IoT) devices. Both technologies have significantly changed IoT data processing possibilities for cloud computing clients.
Here’s an explanation of how edge and fog computing differ, and how they complement each other.
Read more: Top Edge Computing Companies for 2021
What Is the Difference Between Edge Computing and Fog Computing?
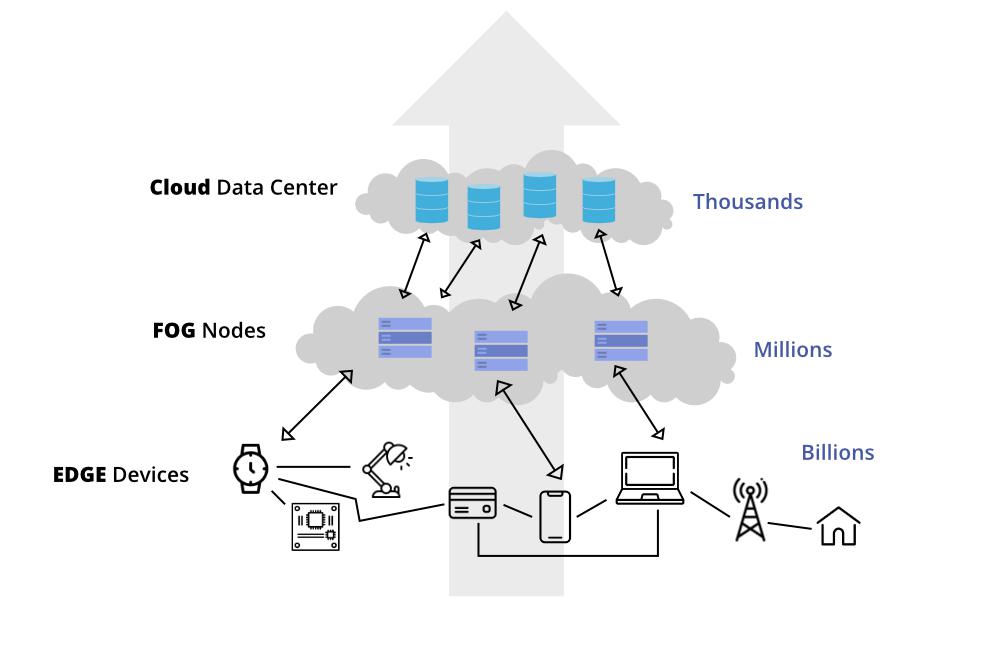
Edge computing and fog computing allow processing data within a local network rather than sending it to the cloud. That benefit decreases latency and increases security. The main difference between the two is processing location.
With edge computing, data processing typically occurs directly on a sensor-equipped product that collects the information or a gateway device physically close to those sensors.
Fog computing moves edge computing activities to LAN hardware or processors connected to it.
Fog computing moves edge computing activities to local area network (LAN) hardware or processors connected to it. These may be physically farther from the data-capturing sensors compared to edge computing.
Jessica Califano, head of marketing and communications at Temboo, clarified, “Fog computing and edge computing are effectively the same thing. Both are concerned with leveraging the computing capabilities within a local network to carry out computation tasks that would ordinarily have been carried out in the cloud.”
It’ll also soon become clear that the most important determination in the edge computing vs fog computing debate is usually not which one is “better.” Ideally, decision-makers should understand what works best for their applications and business structures.
How Do Edge and Fog Computing Make IoT Data Processing More Secure?
As people become more reliant on IoT data and cloud computing, they’re often increasingly aware of the need to keep information as secure as possible — due to what hackers could achieve by exploiting it.
For example, if a manufacturer’s IoT data is stolen, cybercriminals could learn proprietary details about that organization’s production methods.
Read more: Top Cyber Security Threats to Organizations
Keeping Data Moving
Sending data over long distances to the cloud increases the chances of hackers intercepting the data before it arrives at that destination. Cybersecurity expert John Arquilla recently said, “I have a very simple mantra worth remembering: Data at rest are data at risk.” He also confirmed that the location makes a significant difference when people want to keep critical information safe.
“Where should information go to be safe? The best places are in the cloud and ‘the fog.’ Cloud computing is about putting data on someone else’s system, and it is a practice on the rise. Growing comfort with the cloud should encourage a willingness to put even the most sensitive information out on it,” he noted.
‘Data at rest are data at risk.’
Arquilla continued, “The fog is a form of edge computing and consists of those structures between systems that produce data and the cloud. Because it is outside the servers in one’s own data center, the fog offers yet another hiding and storage space that hackers will find hard to access. Both are far better than simply keeping key information close.” Fog computing does not eliminate IoT security risks, but it minimizes them.
Shortening the overall travel time with edge and fog computing makes IoT workload handling safer. However, as Arquilla discussed, edge and fog computing support data decentralization, keeping the information safer.
Making Smarter Data Processing Choices
Fog computing operates within the cloud rather than outside of it. Thus, people may use it to monitor smaller IoT devices that do not have built-in security measures.
It’s also possible to rely on fog computing to simultaneously update IoT devices without requiring they first connect to the cloud. Doing that could keep the respective devices more secure. Another way to protect fog computing is to install virtual firewalls around it.
The rise of the IoT and cloud computing has spurred a related interest in serverless computing. It’s a highly scalable process that tasks cloud providers with all servers and associated management tasks, freeing companies from having on-premise equipment.
Just as there are security risks with sending all data to the cloud, the same is true with processing everything at the edge.
That approach makes sense for many organizations. However, it takes substantial time and effort to design a serverless architecture that performs well and is easily maintained. In most cases, the ideal approach is to decide what data to process in the cloud and what’s better suited for edge and fog computing.
Just as there are security risks with sending all data to the cloud, the same is true with processing everything at the edge. Cloud providers have stringent security protocols that collectively reduce cyberattack risks. It’s not always possible to apply similar measures to edge devices.
Fog and edge computing let service providers filter out sensitive data to be processed locally while handling nonsensitive information in the cloud. That’s useful for industries like health care and retail, which often deal with personal data.
Some applications also demand local data processing to function correctly. For example, the information handling associated with smart assistants often happens directly on the devices. That’s the optimal choice, since people expect prompt answers to their queries.
Read more: Edge Computing Trends in 2021
What Does the Future Hold for Fog and Edge Computing?
Most edge and fog computing use cases relate to the Internet of Things. That’s probably because most research on the matter has so far centered on IoT possibilities. However, that could change as people get more curious about exploring past perceived limits. For example, research from Wayne State University suggests it could improve firefighting.
When crews have accurate, current details before and while fighting a blaze, they’re more likely to succeed in getting it under control, saving lives and preserving property. The research indicated that processing relevant data on a firetruck or within a localized data center could provide the faster speeds necessary when dealing with critical details.
Edge and fog computing could also prove useful for handling the massive amounts of data captured by video cameras at live sporting events. One high-definition camera can generate about 1.8 GB of data each hour, depending on its settings. Processing this information locally — rather than transferring it to the cloud — could improve the experiences of people watching high-profile events, such as the Olympics and the Super Bowl.
Edge Computing vs Fog Computing: Supporting Tech Advancements
As people learn more about edge and fog computing, they’ll achieve a more balanced perspective by not trying to figure out which technology brings superior offerings.
In most cases, these technologies complement each other. Fog and edge computing will push technology and its applications forward for the foreseeable future, particularly when the people using them take the time to understand the advantages they bring.
Read next: Edge Computing: Tips for Hiring and Getting Hired









